We came across the following warning in one of our clusters running ESXi 6.7.0, 17700523 (latest build)
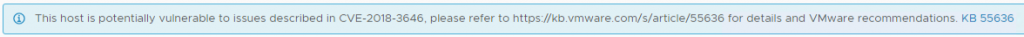
After some searching, performing the following steps from kb article 55806 solved the issue for us.
Enabling the ESXi Side-Channel-Aware Scheduler Version 2 (SCAv2) using ESXi Embedded Host Client
- Connect to the ESXi host by opening a web browser to https://HOSTNAME.
- Click Manage under host navigator.
- Click the Advanced settings Tab.
- Use the search box to find VMkernel.Boot.hyperthreadingMitigation.
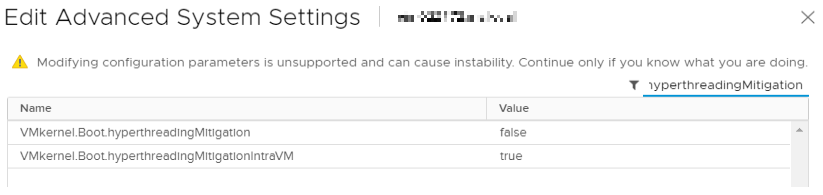
Here you can see that VMkernel.Boot.hyperthreadingMitigation is set to ‘false’
- Select the VMkernel.Boot.hyperthreadingMitigation setting and click the Edit Option.
- Change the configuration option to true (default: false).
- Click Save.

- Use the search box to find VMkernel.Boot.hyperthreadingMitigationIntraVM.
- Select the VMkernel.Boot.hyperthreadingMitigationIntraVM setting and click the Edit Option.
- Change the configuration option to false (default: true).
- Click Save.
- Reboot the ESXi host for the configuration change to go into effect.
As you could see in the ‘Edit Advanced System Settings’ screenshots, VMkernel.Boot.hyperthreadingMitigationIntraVM already had the correct status which is ‘true’.