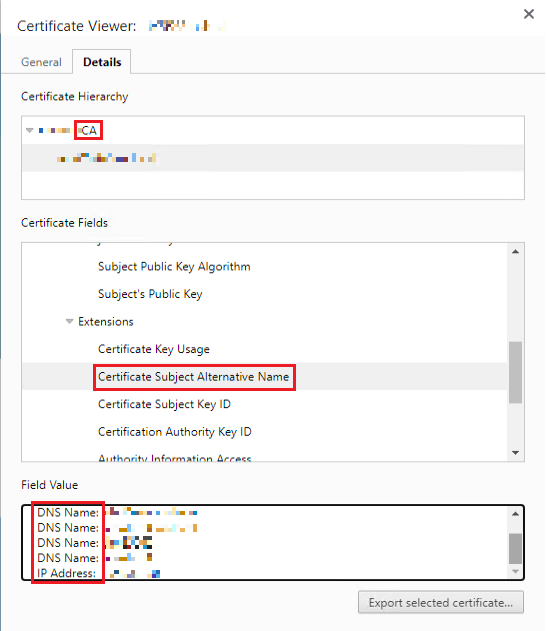
To access your vCenter through a subject alternative name (SAN) other than the vCSA’s FQDN, you can add the desired SAN to the certificate and acquire a secure access to the UI with it.
This is achieved by using the Certificate Manager utility within the vCSA to generate the required certificates that contain the SAN name(s) in it.
Before proceeding with the procedure it would be advisable to perform these steps in a test environment first before implementing this in production and to take a snapshot of the VM.
If your certool.cfg is already in place and there is no need to change the information in this file then you can skip this step.
To deviate from the standard information that comes with the template and change it to the values of your organization, edit the certool.cfg file located in > /usr/lib/vmware-vmca/share/config
As shown in the example here below:
root@vcsa01 [ /usr/lib/vmware-vmca/share/config ]# cat certool.cfg
#
# Template file for a CSR request
#
# Country is needed and has to be 2 characters
Country = NL
Name = CA
Organization = Virtual Stack
OrgUnit = vStack Engineering
State = NH
Locality = Amsterdam
IPAddress = 127.0.0.1
Email = info@vStack.it
Hostname = server.vStack.it
The information provided above will return in a later stage whilst generating the root ca for the vCSA.
Proceed to login to your vCSA through ssh and start the Certificate Manager utility in the following dir > /usr/lib/vmware-vmca/bin
root@vcsa01 [ /usr/lib/vmware-vmca/bin ]# ./certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
| |
| *** Welcome to the vSphere 6.8 Certificate Manager *** |
| |
| -- Select Operation -- |
| |
| 1. Replace Machine SSL certificate with Custom Certificate |
| |
| 2. Replace VMCA Root certificate with Custom Signing |
| Certificate and replace all Certificates |
| |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| |
| 4. Regenerate a new VMCA Root Certificate and |
| replace all certificates |
| |
| 5. Replace Solution user certificates with |
| Custom Certificate |
| NOTE: Solution user certs will be deprecated in a future |
| release of vCenter. Refer to release notes for more details.|
| |
| 6. Replace Solution user certificates with VMCA certificates |
| |
| 7. Revert last performed operation by re-publishing old |
| certificates |
| |
| 8. Reset all Certificates |
|_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _|
Select option 4 and provide the necessary information if needed. Press enter if the default value is correct
Note : Use Ctrl-D to exit.
Option[1 to 8]: 4
Do you wish to generate all certificates using configuration file : Option[Y/N] ? : y
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:administrator@vsphere.local
Enter password:
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : NL] :
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : Virtual Stack] :
Enter proper value for 'OrgUnit' [Default value : vStack Engineering] :
Enter proper value for 'State' [Default value : NL] :
Enter proper value for 'Locality' [Default value : Amsterdam] :
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : *ip address vCenter*
Enter proper value for 'Email' [Default value : info@vstack.it] :
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : vstack.it
Enter proper value for VMCA 'Name' :CA
You are going to regenerate Root Certificate and all other certificates using VMCA
Continue operation : Option[Y/N] ? :
Please enter any value with in [Y/N]. : Option[Y/N] ? : y
When the Regenerate a new VMCA Root procedure is finished a new root.cer file is created. The file is located at > /var/lib/vmware/vmca
root@vcsa01 [ /var/lib/vmware/vmca ]# ls -l
total 112
-rw------- 1 vmcad-user lwis 83968 Sep 15 08:50 certs.db
-rw------- 1 vmcad-user lwis 1703 Sep 15 08:43 privatekey.pem
-rw------- 1 vmcad-user lwis 1703 Sep 15 08:43 privatekey.pem.0
-rw-r--r-- 1 vmcad-user lwis 1420 Sep 15 08:43 root.cer
-rw------- 1 vmcad-user lwis 1490 Sep 15 08:43 root.cer.0
-rw-r--r-- 1 vmcad-user lwis 755 Sep 15 08:50 vmca.crl
-rw-r--r-- 1 vmcad-user lwis 755 Sep 15 08:50 vmca.crl.tmp
Copy the content (BEGIN Certificate till END Certificate) of the root.cer file and paste it in a notepad file, save the file as a .cer file. In our case > vstack.it.cer
root@vcsa01 [ /var/lib/vmware/vmca ]# cat root.cer
Depending on your Organizations Certificate policy, the following may or may not be applicable to you. If, for instance your organization works with GPO to distribute the certificate, you will have to arrange this first before proceeding with step 3 in the Certification Manager utility. If else the vCenter UI will not be available to users due to the absence of the correct certificate.
For our (demonstration) purposes we will continue to manually import the certificate in the “Trusted Root Certification Authorities” folder within certlm on our management server as described below.
Install the newly created .cer certificate file
Select > Open
> Next

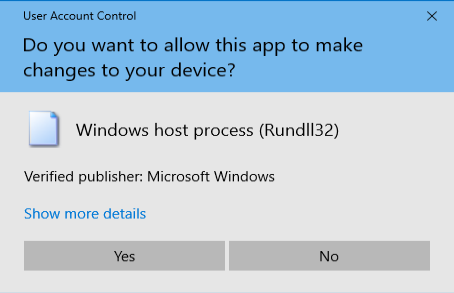
Place all certificates in the following store > Browse
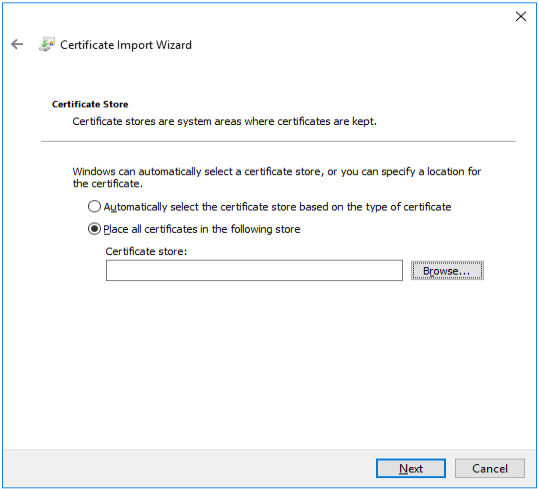
Select “Trusted Root Certification Authorities”
You can view the certificate in certlm. To do this go to > Start > Run > certlm.msc
Find your cert and open it to view the properties.
Next step is to perform option 3 within the Certification Manager utility, which is “Replace Machine SSL Certificate with VMCA Certificate”
This step is important as for the SAN(‘s) are added here. First the FQDN then the SAN value(s), comma seperated as shown in the example text below stated in bold.
root@vcsa01 [ /usr/lib/vmware-vmca/bin ]# ./certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
| |
| *** Welcome to the vSphere 6.8 Certificate Manager *** |
| |
| -- Select Operation -- |
| |
| 1. Replace Machine SSL certificate with Custom Certificate |
| |
| 2. Replace VMCA Root certificate with Custom Signing |
| Certificate and replace all Certificates |
| |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| |
| 4. Regenerate a new VMCA Root Certificate and |
| replace all certificates |
| |
| 5. Replace Solution user certificates with |
| Custom Certificate |
| NOTE: Solution user certs will be deprecated in a future |
| release of vCenter. Refer to release notes for more details.|
| |
| 6. Replace Solution user certificates with VMCA certificates |
| |
| 7. Revert last performed operation by re-publishing old |
| certificates |
| |
| 8. Reset all Certificates |
|_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _|
Choose option 3 > “Replace Machine SSL certificate with VMCA Certificate’“
Note : Use Ctrl-D to exit.
Option[1 to 8]: 3
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:Administrator@vsphere.local
Enter password:
certool.cfg file exists, Do you wish to reconfigure : Option[Y/N] ? : y
Press Enter key to skip optional parameters or use Previous value.
Enter proper value for 'Country' [Previous value : NL] :
Enter proper value for 'Name' [Previous value : CA] :
Enter proper value for 'Organization' [Previous value : Virtual Stack] :
Enter proper value for 'OrgUnit' [Previous value : vStack Engineering] :
Enter proper value for 'State' [Previous value : NH] :
Enter proper value for 'Locality' [Previous value : Amsterdam] :
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : *vcsa ip address*
Enter proper value for 'Email' [Previous value : info@vstack.it] :
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : vstack.it,vstack
Enter proper value for VMCA 'Name' :CA
You are going to regenerate Machine SSL cert using VMCA
Continue operation : Option[Y/N] ? : y
Get site nameompleted [Replacing Machine SSL Cert...]
default-first-site
Lookup all services
Get service default-first-site:36457dd7-60f1-42ba-b795-f14ea1476063
Update service default-first-site:36457dd7-60f1-42ba-b795-f14ea1476063; spec: /tmp/svcspec_ncoq6gs8
Get service default-first-site:9c695cac-7ad1-4c86-86d8-91d5bceb8bde
Update service default-first-site:9c695cac-7ad1-4c86-86d8-91d5bceb8bde; spec: /tmp/svcspec_y_tozrgq
Get service default-first-site:74cf68be-3eae-4216-a987-ee8c4e439f61
Update service default-first-site:74cf68be-3eae-4216-a987-ee8c4e439f61; spec: /tmp/svcspec_0um_cgva
When step 3 is finished, navigate to your browser > vCenter UI > Connection security settings (lock) > and check the certificate to see if the SAN value(s) are added here. You can now access your vCenter through the newly added SAN(‘s), make sure that the SAN names are added in DNS.